The Authentication Dilemma: Choosing Between JWT and OAuth
- General
- Performance and Security
The Authentication Dilemma: Choosing Between JWT and OAuth
JWT Authentication: the ins and outs
JWT provides a stateless mechanism for securely transmitting information between parties as a JSON object. In this blog post, we’ll delve into the intricacies of JWT authentication and demonstrate its implementation in a Django application.
Understanding JWT Authentication
JSON Web Tokens consist of three parts: header, payload, and signature. These parts are concatenated with dots to form a token in the following format: header.payload.signature.
Header
The header contains:
- type: the specification that the token is a JWT
- algorithm: the signing algorithm used to sign said token
Algorithms that are used to sign include RSA, HMAC, or SHA256. The signatures for the tokens serve two purposes – integrity and authenticity.
Payload
The payload contains the intended messages which are commonly known as claims and metadata, as well as any other information.
There are three types of claims:
- Registered claims: they include
exp(expiration time),iss(issuer),sub(subject) andaud(audience). They are highly recommended since they provide information on the use and condition of use of the token. - Public claims: these are claims that are unique to avoid collisions with other services that use JWT.
- Private claims: these are claims that are used specifically between two parties that understand the meaning and use. Like the example of my medals, my games master and I understood the value.
Signature
- To create the signature part, the header and payload are encoded using a base64 algorithm and concatenated with a period (.). This string is then encrypted with a secret key using the algorithm specified in the header.
- The signature verifies that information is only accessed by authorised people. It is issued by the JWT backend using base64 + payload + secrect_key.
- The signature is verified for each request. To validate the signature, you use the secret_key. Remember the purpose of having it called secret_key is so that it is secret.
- If you have a json web token and want to segregate it’s different parts to know what each part means, you can go to this website: https://jwt.io/ and enter your encoded token, it’ll decode the token into header, payload and signature.
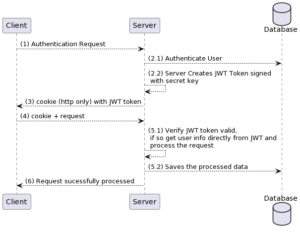
JWT Implementation in Django
To implement JWT in Django, we’ll use the djangorestframework-simplejwt package.
Install the Package
|
1 |
pip install djangorestframework-simplejwt |
Configure Django Settings
In settings.py, add the following configurations:
|
1 2 3 4 5 6 7 8 9 10 11 |
INSTALLED_APPS = [ ... 'rest_framework', 'rest_framework_simplejwt', ] REST_FRAMEWORK = { 'DEFAULT_AUTHENTICATION_CLASSES': ( 'rest_framework_simplejwt.authentication.JWTAuthentication', ), } |
Set Up URLs:
In your urls.py, include the JWT views:
|
1 2 3 4 5 6 7 8 9 10 11 |
from django.urls import path from rest_framework_simplejwt.views import ( TokenObtainPairView, TokenRefreshView, ) urlpatterns = [ ... path('api/token/', TokenObtainPairView.as_view(), name='token_obtain_pair'), path('api/token/refresh/', TokenRefreshView.as_view(), name='token_refresh'), ] |
Protecting Views
In your views, use the @api_view decorator and ensure authentication is required:
|
1 2 3 4 5 6 7 8 |
from rest_framework.decorators import api_view, permission_classes from rest_framework.permissions import IsAuthenticated from rest_framework.response import Response @api_view(['GET']) @permission_classes([IsAuthenticated]) def protected_view(request): return Response({"message": "This is a protected view"}) |
Trade-Offs of JWT
Pros:
- Stateless: No need to store session information on the server.
- Scalability: Suitable for distributed systems.
- Compact: Efficient to transmit over the network.
Cons:
- Security: If not handled properly, JWT can be vulnerable to attacks (e.g., token leakage).
- Revocation: Difficult to invalidate a token before it expires without additional mechanisms.
OAuth: Open Authentication
What is OAuth?
OAuth is an open standard for access delegation, commonly used for token-based authentication and authorization. It allows third-party services to exchange information on behalf of the user without exposing their credentials.
How OAuth Works
- Resource Owner: The user who authorizes access to their data.
- Client: The application requesting access.
- Authorization Server: The server that issues access tokens after authenticating the resource owner and obtaining authorization.
- Resource Server: The server hosting the protected resources.
OAuth Implementation in Django:
To implement OAuth in Django, we can use the django-oauth-toolkit package.
Install the Package
|
1 |
pip install django-oauth-toolkit |
Configure Django Settings
In settings.py, add the following configurations:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
INSTALLED_APPS = [ ... 'oauth2_provider', ] REST_FRAMEWORK = { 'DEFAULT_AUTHENTICATION_CLASSES': ( 'oauth2_provider.contrib.rest_framework.OAuth2Authentication', ), 'DEFAULT_PERMISSION_CLASSES': ( 'rest_framework.permissions.IsAuthenticated', ) } OAUTH2_PROVIDER = { 'ACCESS_TOKEN_EXPIRE_SECONDS': 36000, 'APPLICATION_MODEL': 'yourapp.Application', } |
Set Up URLs:
In your urls.py, include the OAuth URLs:
|
1 2 3 4 5 6 |
from django.urls import path, include urlpatterns = [ ... path('o/', include('oauth2_provider.urls', namespace='oauth2_provider')), ] |
Protecting Views:
In your views, use the @api_view decorator and ensure authentication is required:
|
1 2 3 4 5 6 7 8 |
from rest_framework.decorators import api_view, permission_classes from rest_framework.permissions import IsAuthenticated from rest_framework.response import Response @api_view(['GET']) @permission_classes([IsAuthenticated]) def protected_view(request): return Response({"message": "This is a protected view"}) |
Trade-Offs of OAuth
Pros:
- Enhanced Security: OAuth eliminates the need for users to share their credentials with third-party applications, reducing the risk of password theft and unauthorized access.
- User Convenience: Users can easily grant and revoke access to their data without sharing their passwords, improving convenience and trust.
- Scalability: OAuth’s token-based approach allows for scalable authentication and authorization across distributed systems, supporting a large number of users and services.
- Single Sign-On (SSO): OAuth enables Single Sign-On capabilities, allowing users to access multiple services with a single set of credentials, enhancing user experience and productivity.
- Standardization: OAuth is an open standard with widespread adoption, providing interoperability between different platforms and services, and reducing vendor lock-in.
- Authorization Control: OAuth allows fine-grained control over the scope of access granted to third-party applications, enabling users to specify which resources an application can access.
Cons:
- Complexity: Implementing OAuth can be complex, especially for developers new to the concept, requiring an understanding of various grant types, flows, and security considerations.
- Dependency on Third-Party Providers: OAuth relies on third-party identity providers for authentication and authorization, introducing dependencies and potential risks if providers experience downtime or policy changes.
- User Experience: Redirecting users to external login pages for authentication can disrupt the user experience and lead to confusion or distrust if not implemented properly.
- Granularity of Permissions: OAuth scopes may not always offer granular control over permissions, leading to situations where applications request more access than necessary, potentially exposing sensitive data.
- Token Management: Managing access tokens securely, including their expiration, revocation, and storage, can be complex and require additional overhead.
JWT is best used in scenarios where:
- Stateless Authentication: It’s great for applications that require stateless authentication, as JWTs contain all necessary information within the token itself, reducing the need for server-side storage.
- Microservices Architecture: In architectures with multiple independent services, JWTs offer a lightweight authentication mechanism without the need for centralized session management.
- Mobile and Single-Page Applications: JWTs are commonly employed in mobile and single-page applications, where traditional session-based authentication may not be suitable due to their stateless nature.
- Scalability: JWTs can enhance scalability by minimizing server-side load, as they eliminate the need for accessing a central session store during token verification.
- Custom Claims: JWTs allow for the inclusion of custom claims, providing flexibility to encode additional user information or metadata within the token.
OAuth:
OAuth is ideal in situations where:
- Authorization Delegation: It’s designed for scenarios where users delegate authorization to third-party applications, allowing them to access resources on behalf of the user with their consent.
- API Access Control: OAuth secures access to APIs, permitting clients to acquire access tokens with specific scopes defining their level of access to protected resources.
- Single Sign-On (SSO): OAuth can implement Single Sign-On (SSO), enabling users to authenticate once and access multiple services without re-entering credentials.
- Third-Party Integration: It facilitates secure integration with third-party platforms by letting users grant limited access to their resources without exposing their credentials.
- Centralized Authorization Server: OAuth typically involves a centralized authorization server that issues access tokens and enforces access control policies, making it suitable for scenarios where centralized control is preferred.
In summary, JWTs excel in stateless authentication scenarios like microservices and mobile apps, while OAuth is more suited for authorization delegation, API access control, SSO, and third-party integrations.
References and Additional Resources
For further reading and a deeper understanding of JWT and OAuth authentication, consider exploring these resources:
- OAuth vs JWT: A Detailed Comparison – An in-depth analysis of the differences between OAuth and JWT.
- Why OAuth is Better than Basic Authentication – Explores the advantages of OAuth over traditional authentication methods.
- OAuth vs JWT: Which One Is Better For Authentication? – A comprehensive comparison of OAuth and JWT for authentication purposes.
- “The OAuth 2.0 Authorization Framework” – RFC 6749, Internet Engineering Task Force (IETF). Available at: https://tools.ietf.org/html/rfc6749
- “JSON Web Token (JWT)” – RFC 7519, Internet Engineering Task Force (IETF). Available at: https://tools.ietf.org/html/rfc7519
- Schwartz, A. (2019). “OAuth 2.0 for Native Apps”. O’Reilly Media, Inc.
- Jones, M., & Hardt, D. (2012). “The OAuth 2.0 Authorization Framework: Bearer Token Usage”. RFC 6750, Internet Engineering Task Force (IETF).
- Lodderstedt, T., McGloin, M., & Hunt, P. (2013). “OAuth 2.0 Threat Model and Security Considerations”. RFC 6819, Internet Engineering Task Force (IETF).
These resources provide a mix of practical guides, detailed comparisons, and academic references to deepen your understanding of JWT and OAuth authentication mechanisms.
Hope you have a good read!
Related content
Auriga: Leveling Up for Enterprise Growth!
Auriga’s journey began in 2010 crafting products for India’s
