How SSL Certificate safeguards the communication
- Digital Engineering
- General
- Performance and Security
How SSL Certificate safeguards the communication
What is SSL
SSL certificates have become the necessity now. Browsers have stopped entertaining the web applications without SSL certificates. It is security protocol that enables encrypted communication. With SSL you can be confident that –
• No one has read your message
• No one has changed your message
• You are communicating with the intended person (server)
SSL Certificate Generation
• Generate a private-public key pair.
• Create a CSR (certificate signing request) and share with Certificate Authority (CA)
• CA signs the CSR using CA’s private key and attach its Digital Signature.
• CA shared server certificate, Root and intermediate certificate.
• Above certificate files can be configured/installed with webserver and you are done.
SSL certificates includes
•Server Certificate with Name of the certificate holder, the certificate’s serial number and expiration date , a copy of the certificate holder’s public key, the digital signature of the certificate-issuing authority.
• Root Certificate, Intermediate Certificate (or a bundle ) to build chain of trust
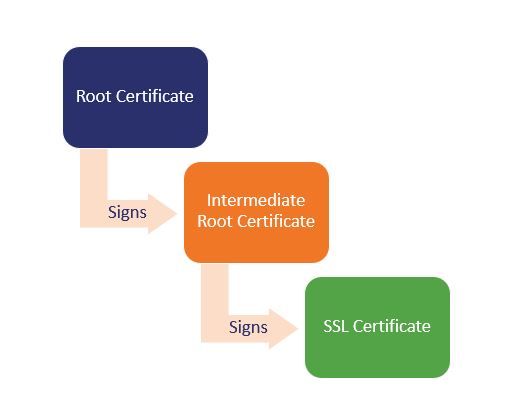
Chain of Trust – Root & Intermediate Certificate
Root Certificate – A root certificate is a digital certificate that belongs to the issuing Certificate Authority. It comes pre-downloaded in most browsers and is stored in what is called a “trust store.” The root certificates are closely guarded by the Certificate Authorities.
Certificate Authorities do not issue server/leaf certificates (end user SSL certificates) directly off of their roots. Those roots are too valuable and there’s just too much risk.
So, to insulate themselves, CAs generally issue what is called an intermediate root. The CA signs the intermediate root with its private key, which makes it trusted. Then the CA uses the intermediate certificate’s private key to sign and issue end user SSL certificates. This process can play out several times, where an intermediate root signs another intermediate and then a CA uses that to sign certificate. These links, from root to intermediate to leaf – are the certificate chain.
Here’s a visualization of a certificate chain using one intermediate crt.
How browser verifies the SSL
When you install your SSL certificate, you’ll also be sent an intermediate root certificate or bundle. When a browser downloads your website’s SSL certificate upon arriving at your homepage(during SSL handshaking) , it begins chaining that certificate back to its root. It will begin by following the chain to the intermediate that has been installed, from there it continues to tracing backwards until it arrives at a trusted root certificate. If the certificate is valid and can be chained back to a trusted root, it will be trusted. If it can’t be chained back to a trusted root, the browser will issue a warning about the certificate.
SSL Handshaking Process
Lets try to understand what all happens during the SSL Handshake –
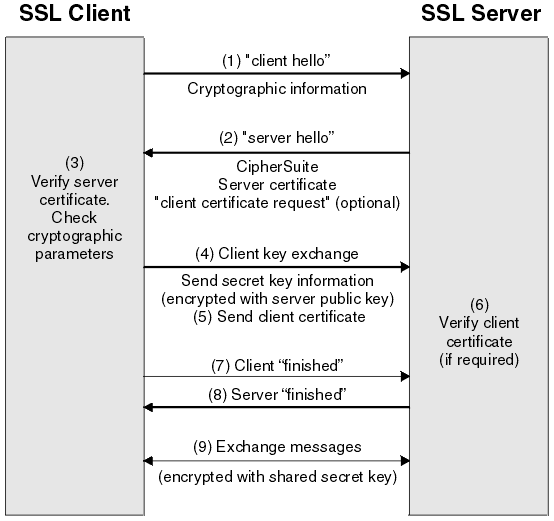
1. Browser connects to server Using SSL (https)
2. Server Responds with Server Certificate containing the public key of the web server.
3. Browser verifies the certificate by checking the signature of the CA. To do this the CA certificate needs to be in the browser’s trusted store. Client certificates are also verified by server in case of Mutual SSL.
4. TLS client generates random byte string that enables both the client and the server to compute the secret key to be used for encrypting subsequent message data. The random byte string itself is encrypted with the server’s public key.
5. The SSL or TLS client sends the server a finished message, which is encrypted with the secret key, indicating that the client part of the handshake is complete.
6. The SSL or TLS server sends the client a finished message, which is encrypted with the secret key, indicating that the server part of the handshake is complete.
References –
https://www.ibm.com/support/knowledgecenter/en/SSFKSJ_7.5.0/com.ibm.mq.sec.doc/q009930_.html
https://www.thesslstore.com/blog/root-certificates-intermediate/
https://www.thesslstore.com/knowledgebase/ssl-support/explaining-the-chain-of-trust/
Related content
Auriga: Leveling Up for Enterprise Growth!
Auriga’s journey began in 2010 crafting products for India’s

