How to install and configure Ansible
- Performance and Security
How to install and configure Ansible
What is Ansible ?
Ansible is a simple open source IT engine which automates application deployment, intra-service orchestration,configuration management and many other IT needs. Ansible is easy to deploy because it does not use any agents or custom security infrastructure.
Ansible is a push based configuration management tool which means that we can directly push all the configuration on to the host machine directly.
Ansible uses playbook to describe automation jobs, and playbook uses very simple language i.e. YAML which is very easy for humans to understand, read and write. Hence the advantage is that even the IT infrastructure support guys can read and understand the playbook and debug if needed (YAML – It is in human readable form).
Features of Ansible
- Simple to install and setup and very easy to learn.
- No need for any agent or client software to manage the nodes, all that we need to install ansible on the control machine and make ssh connection with your nodes and start pushing configuration right away.
- Capabilities to model complex IT workflows .
- Ansible modules can be extended and modified and we can modify them in any programming language.
Ansible Architecture
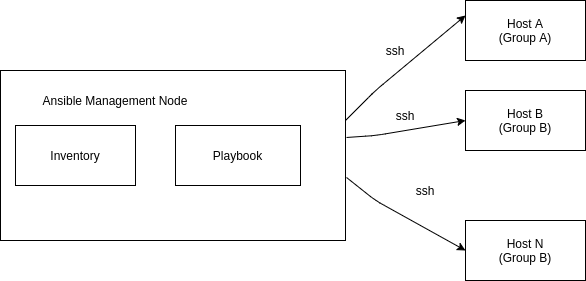
The picture shown below show how ansible works
Ansible works by connecting to your nodes and pushing out small programs, called “Ansible modules” to them. Ansible then executes these modules (over SSH by default), and removes them when finished. Your library of modules can reside on any machine, and there are no servers, daemons, or databases required.
The management node in the above picture is the controlling node (managing node) which controls the entire execution of the playbook. It’s the node from which you are running the installation.The Ansible management node is the machine we will use to connect to and control the Ansible hosts over SSH. Your Ansible management node can either be your local machine or a server dedicated to running Ansible
Inventory is a file which contains the list of all IP addresses of all host machines.
Playbook describes the whole workflow of system.Playbook contains a set of place which are set of tasks and inside every task there is particular module so when we run a playbook it’s the modules that actually get executed on all your node machine
Ansible host is any machine that your Ansible control node is configured to automate.
Ansible Installation
- Go to ansible control node and set its non-root user with sudo privileges. To set this up,
- Create new user
1$ adduser username
- Granting Administrative Privileges
As root, run this command to add your new user to the sudo group1$ usermod -aG sudo username
- Create new user
- Generate SSH keypair for this user. To set this up, you can follow Step 1 of link How to Set Up SSH Keys on Ubuntu 18.04
- Go to ansible host node and add Ansible control node SSH public key to the authorized_keys of hosts.This we can add by following Step 2 of link How to Set up SSH keys on Ubuntu 18.04
- Installing Ansible on Control node
We can setup ansible by running following commands:123$ sudo apt-add-repository ppa:ansible/ansible$ sudo apt update$ sudo apt install ansible - Setup Inventory file on Control node
Inventory file contains information about the hosts that you will manage through ansible.Inventory file contains any number of hosts that can be organized under groups and subgroups.Edit the content of default inventory file presentOr we can create new inventory file and provide its path using parameter -iThe default inventory file provided by the Ansible installation contains a number of examples that you can use as references for setting up your inventory. The following example defines a group named [servers] with three different servers in it, each identified by a custom alias: server1, server2, and server3. Be sure to replace the highlighted IPs with the IP addresses of your Ansible hosts.1$ sudo nano /etc/ansible/hostsNow save the file123456[servers]server1 ansible_host=203.0.113.111server2 ansible_host=203.0.113.112server3 ansible_host=203.0.113.113[all:vars]ansible_python_interpreter=/usr/bin/python3 - Testing Connection From your local machine run :
This command will use Ansible’s built-in ping module to run a connectivity test on all nodes from your default inventory, connecting as root. The ping module will test:1$ ansible all -m ping -u root
- if hosts are accessible.
- if you have valid SSH credentials.
- if hosts are able to run Ansible modules using Python.
You should get output similar to this:
12345678910111213Outputserver1 | SUCCESS => {"changed": false,"ping": "pong"}server2 | SUCCESS => {"changed": false,"ping": "pong"}server3 | SUCCESS => {"changed": false,"ping": "pong"} - Writing Playbook File
For actual server setup we write playbook file.Playbook file is YAML file that contains a series of task that needs to be executed on host machine
Task Format
A task defines a single automated step that should be executed by Ansible. It typically involves the usage of a module or the execution of a raw command. This is how a task looks:12- name: This is a taskapt: name=vim state=latestThe name part is actually optional, but recommended, as it shows up in the output of the provisioning when the task is executed. The apt part is a built-in Ansible module that abstracts the management of packages on Debian-based distributions. This example task tells Ansible that the package vim should have its state changed to latest, which will cause the package manager to install this package in case it is not installed yet.
Playbook Format
Playbooks are YAML files containing a series of task to automate the setup of a server.Task are executed in the order in which we have written them in the file. The following example is a simple playbook that perform two tasks: updates the apt cache and installs vim afterwards:123456789---- hosts: alltasks:- name: Update apt-cacheapt: update_cache=yesbecome: yes- name: Install Vimapt: name=vim state=latestbecome: yesLet’s describe this playbook in more detail:
hosts: all
The playbook starts by stating that it should be applied to all hosts in your inventory (hosts: all). It is possible to restrict the playbook’s execution to a specific host, or a group of hosts. This option can be overwritten at execution time.
become: true
The become: true portion tells Ansible to use sudo permission for executing all the tasks in this playbook.
tasks
The section where the actual tasks are defined. The first task updates the apt cache, and the second task installs the package vim. - Running a Playbook
The following command will execute the playbook on all hosts from your default inventory file, using SSH keypair authentication to connect as the current system user:1$ ansible-playbook playbook.ymlYou can also use -l to limit execution to a single host or a group of hosts from your inventory:
1$ ansible-playbook -l host_or_group playbook.ymlIf you need to specify a different SSH user to connect to the remote server, you can include the argument -u user to that command:
1$ ansible-playbook -l host_or_group playbook.yml -u remote-userIf you need to specify a different inventory file, you can use -i to specify different inventory file path:
1$ ansible-playbook -i inventory_file.ini playbook.yml
E.g Install Nginx on Hosts
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
--- - hosts: all tasks: - name: ensure nginx is at the latest version apt: name=nginx state=latest become: yes - name: start nginx service: name: nginx state: started become: yes - name: copy the nginx config file and restart nginx copy: src: /var/www/html/ansible/static_site.cfg dest: /etc/nginx/sites-available/static_site.cfg become: yes - name: create symlink file: src: /etc/nginx/sites-available/static_site.cfg dest: /etc/nginx/sites-enabled/default state: link become: yes - name: copy the content of the web site copy: src: /var/www/html/ansible/static-site-src/ dest: /home/kamal/static-site - name: restart nginx service: name: nginx state: restarted become: yes |
Related content
Auriga: Leveling Up for Enterprise Growth!
Auriga’s journey began in 2010 crafting products for India’s