Our insightful blogs
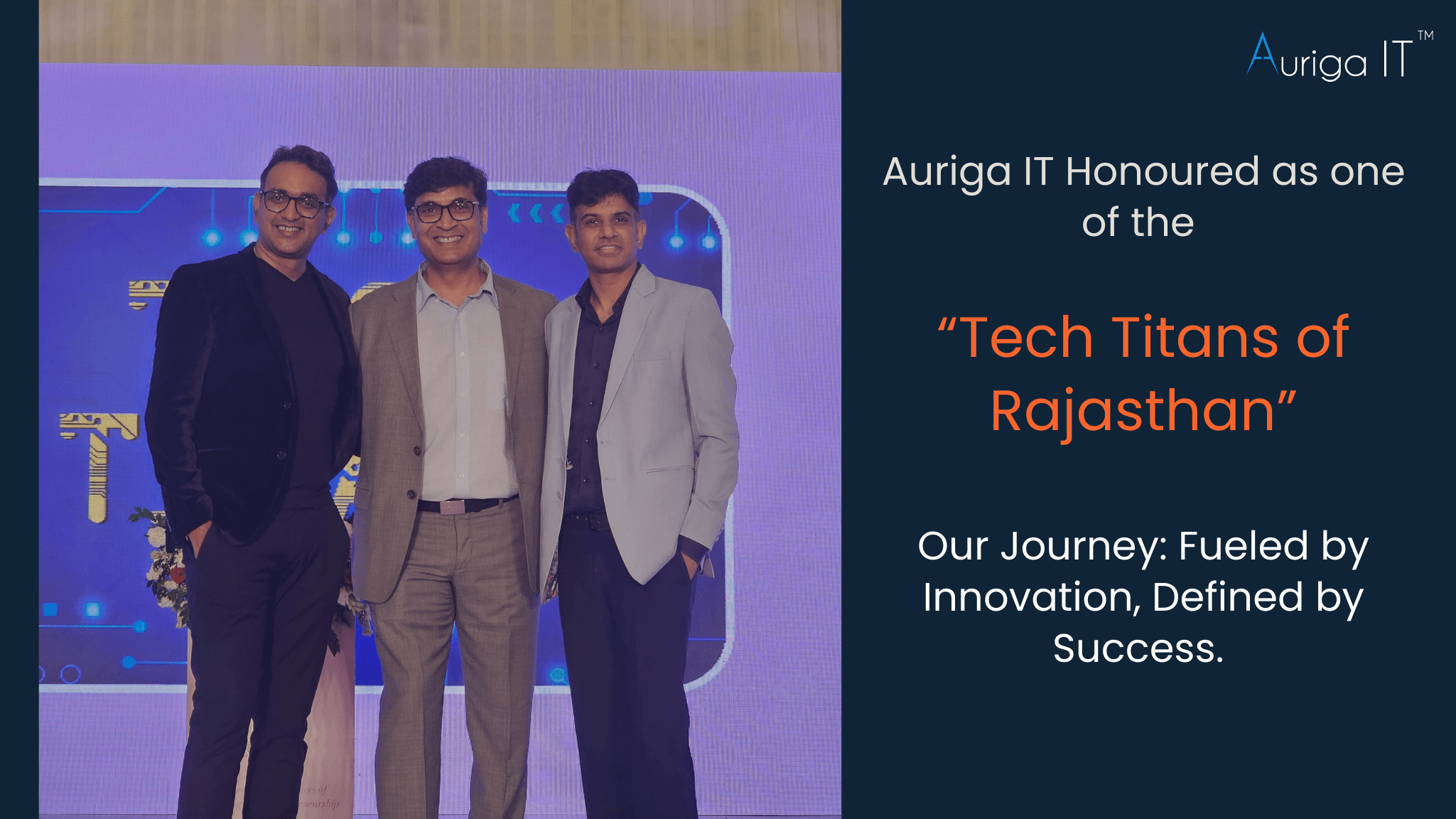
On 26th July 2025, Auriga IT was named a 'Tech Titan of Rajasthan'—a milestone born from a basement startup, friendship, and relentless grit. The morning of 26th July 2025, something
- News & Events
ERPNext, built on the Frappe framework, is an incredibly versatile open-source ERP solution. While its core functionality addresses business needs right out of the box, the default UI may not
Managing HR and Payroll for large operational workforces in India is uniquely complex. Between shifting labor laws, multi-tiered workforce structures, attendance challenges, and contractor payouts—most software systems fall short. At
Unit testing isn’t just about catching bugs — it’s a mindset that helps you write cleaner, more maintainable, and bug-resistant code from the start. When building Django applications, adopting pytest
- General
- Quality Engineering
Every quarter at Auriga feels like the next episode of a great series—complete with lots of action, excitement, major launch moments and of course, plenty of snack breaks. As we
- General
In the era of generative AI, Large Language Models (LLMs) like GPT-4, Claude, and Gemini are transforming the way we interact with technology. But even these powerful models have limitations—especially
We’re in the midst of a language revolution. AI is no longer some abstract concept — it’s here, embedded in our daily lives. From writing emails and summarizing articles to
- Data, AI & Analytics
Supercharging Live Alerts With Redis And Kafka Optimizing Live Alerts with Kafka and Redis Introduction Real-time systems demand both speed and reliability, especially when dealing with high-frequency sensor data.